Most of us rely on online services for our daily life, from keeping in touch with friends to paying bills to setting up a doctor’s appointment. If you are like me, the years of being online has resulted in substantial account sprawl. Since each online account represents a risk for our personal information to be exposed in some malicious way - e.g. account hijacking, financial theft, reputation damage, blackmail - this month I took on a long overdue project: updating my online security.
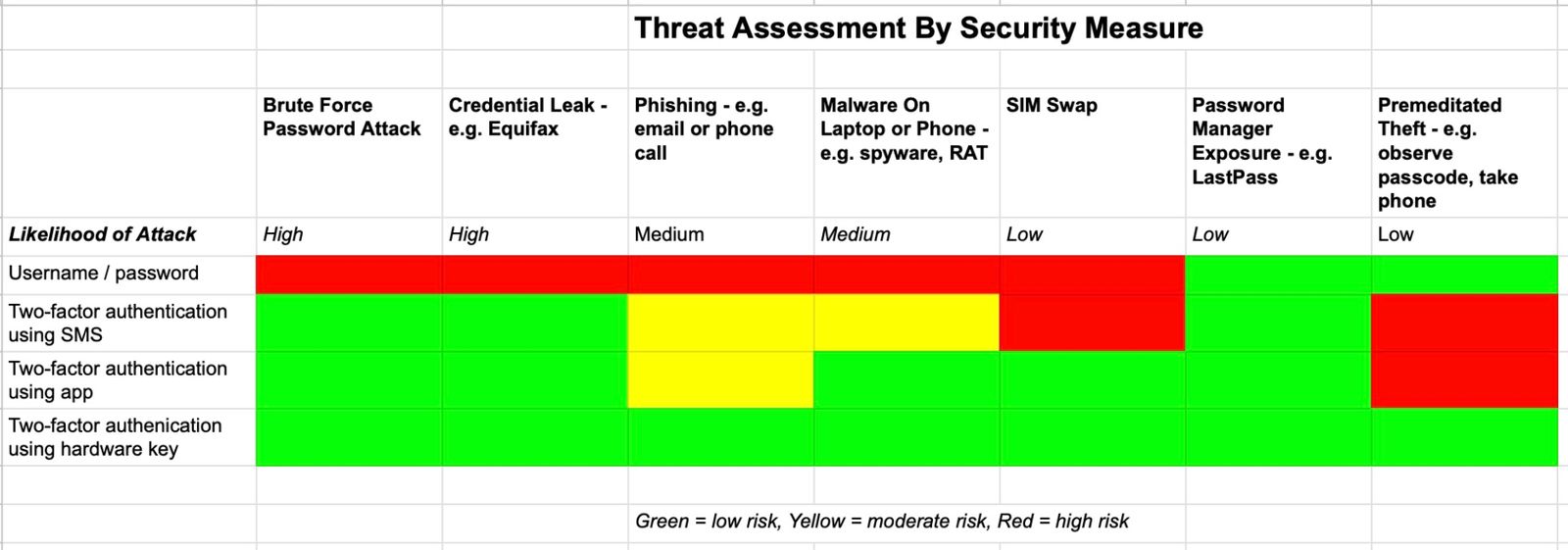
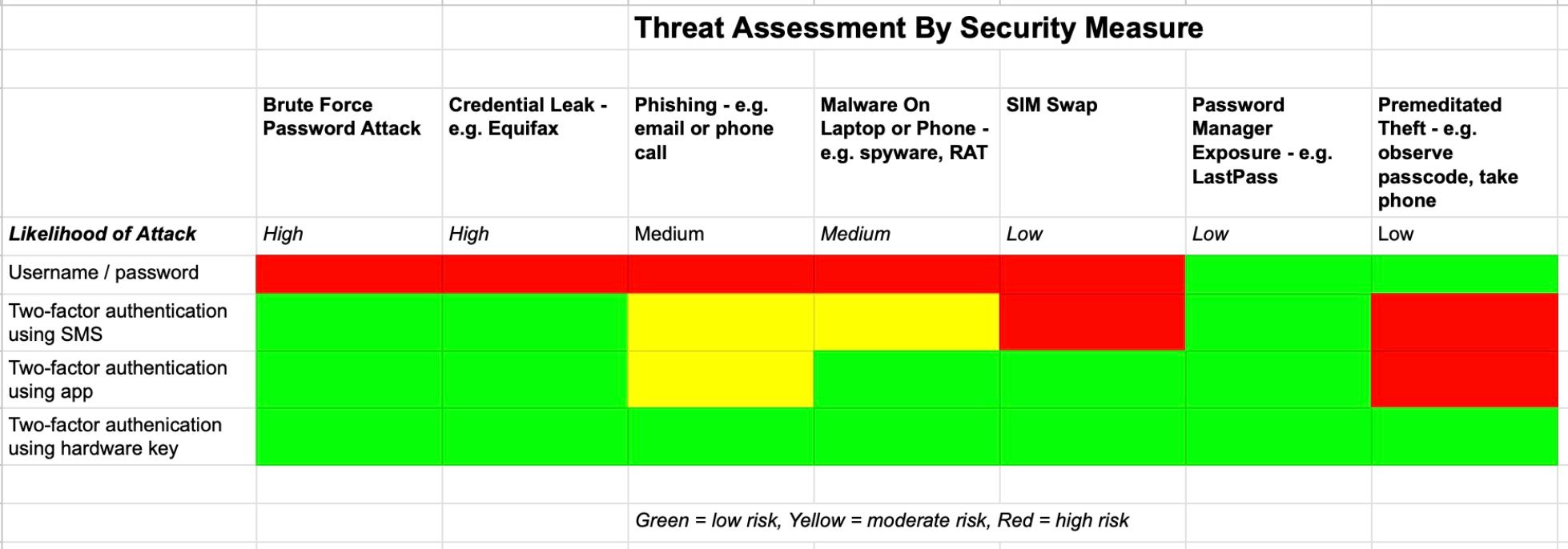
The lapsed CISSP in me couldn't help but create a threat matrix to ensure I understood the potential risks and how best to protect against them. You can safely ignore this chart if it seems like overkill. 😉
While I made a lot of changes as part of this project, there are 5 essential ones I’d recommend everyone consider ASAP.
#1: Identify & Classify All Accounts
I had accumulated over 300 active accounts in my almost 30 years of being online. While the majority of these accounts I hadn’t used in years, they still contained personal information I might not want exposed. For example, I found an account with a company that had my blood test results, another with pay stubs from a previous employer, and yet another with my old prescriptions. You should never assume that just because you don’t use an account anymore, it does not represent a risk.
To find all these accounts, I had to search across my browser history, old emails, and previous password managers. This was the longest and most tedious part of my project, but one that was essential to all my subsequent changes. I maintained a list of all my accounts, classifying each one based on the impact it would have on me in the event it was compromised (high, medium, low). This risk factor came in handy later, since it allowed me to spend more time securing my higher risk accounts.
#2: Rotate All Passwords & Delete Old Accounts
Once I had identified my 300+ accounts, I went through each one to ensure they had a unique and strong password. Over the years I had used a variety of approaches to securing accounts, some of which resulted in me sharing passwords across different services. Some of these passwords were exposed in one of the many high profile data leaks that have occurred over the years from well known companies such as Facebook, Equifax, Home Depot, eBay, and Microsoft - making it more likely a hacker would try these shared passwords to break into my other accounts. Equifax wins the prize for account breaches though, since they offer a $29.95 per month fraud protection service to monitor for the very type of fraud their data leak enabled. To add insult to injury, over six years after the breach they still only allow you to protect your account with a simple username / password.
In rotating my passwords, I chose to consolidate them into a single password manager to make it easier for me going forward. A password manager is software that stores your account credentials securely in a centralized place, making it easy for you to login to different apps and services. If you are using multiple online accounts and not already using a password manager, you really should start today. I had used several over the years, but never took the time to consolidate all of my accounts into a single password manager. I will leave it to you to choose the password manager that best suits your needs / price point - e.g. 1Password, BitWarden, Proton Pass, LastPass (hint: might not want to use LastPass). There are also basic free password managers built into browsers such as Safari or Chrome that work for many use cases, although they lack some of the security and resiliency features that come with standalone services.
After rotating all the passwords, I took the time to delete accounts I never planned to use again. This brought me from 300+ accounts to under 200. This also brought me from a severe online hoarder to just a moderate one.
#3: Secure Accounts With 2FA Where Possible
Most of us realize that using just a username and password to secure an account is no longer sufficient in 2024. I am sure I am not the only one who gets regular posts from Facebook friends whose accounts were hacked. The best way to secure an account today is to use two-factor authentication (2FA). If you have ever been asked to enter a code that was texted to your mobile phone via SMS, you are already familiar with one form of two-factor authentication. While SMS is the most commonly available two-factor authentication for most services, it is unfortunately also the least secure (although definitely much more secure that just a username / password, so use it when it is your only option). Hackers can use “SIM swapping” - i.e. calling a mobile company to impersonate you in order to convince them to swap your current SIM card with one they already own - in order to take over your mobile number, receive your texts, and possibly even restore all your information via a cloud backup. One researcher found that SIM swappers were successful in 78% of their attempts to take over a phone, making this one of the more successful approaches hackers can use to access your accounts.
A better approach to 2FA is to use an authenticator app such as Google Authenticator or Twilio Authy. These provide additional security since the codes you enter come from an app on your phone, thus requiring thieves to have access to one of your devices in order to compromise an account. While I have been using 2FA for a decade now, I found several services I regularly used that were not 2FA enabled. In a few cases this was because I overlooked them, but in others it was just a feature that was not available the last time I reviewed my security. In my project, I found that 58% of the apps / services that I use offered some level of multi-factor authentication - with 65% of these supporting either authenticator apps (72%) and/or security keys (28%).
Setting up 2FA takes only a few minutes and adds a substantial amount of security to an online account. Just make sure you have a clear understanding for each service of how you can recover your account in the event you lose your authenticator app (typically done via one-time backup codes you store safely away).
#4: Use Hardware Key For Critical Accounts
My greatest online risk comes from three accounts: a) financial services (e.g. bank, 401K, payment apps, brokerage), b) my primary email, and c) my Apple ID. While the first is obvious: if a hacker were to gain access to your bank account or 401K, they can drain your life savings with a simple wire transfer. But if a hacker gains access to your primary email and/or Apple ID, they immediately have access to a wealth of personal information and the primary means of communication for all your accounts. This can be used to reset passwords, and to launch a variety of other nefarious attacks on you, your friends and/or family. A financial advisor recently told me the story of a client who requested a wire transfer. On calling the client back, they discovered the request had actually been sent by a hacker who had taken over the client's email account.
While using a 2FA authenticator app for securing these accounts is sufficient for almost all use cases, I decided to upgrade my security here and go with a hardware key. If you are not already familiar with hardware keys - e.g. Yubikey, Google Titan - they are devices you carry with you that provide your devices with the requested unique code you would typically get from an authenticator app or a text message. They are substantially more secure than SMS for 2FA since a hacker would require physical access to your key, and also more secure than authenticator apps since you never view / enter the codes required to validate your accounts (hackers commonly use phishing techniques to gain access to authenticator app codes).
Unfortunately one of the ironies of the financial services industry is that many companies do not support higher levels of security - e.g. authenticator apps, hardware keys. For example, a payment app like Venmo can only be secured with SMS two-factor authentication, which as we discussed can be circumvented by a determined SIM swapper. But I was fortunate to find that almost all my critical accounts supported hardware keys. If you decide to go with security keys, make sure to buy two in order to have a backup in the event you lose one.
#5: Securing Devices
I access my accounts from my laptop, tablet and mobile phone. While I have usually maintained good security practices on my laptop - e.g. firewall, security scanner, encrypted backups - I was surprised at how lax I had become with my phone and tablet. This is made much worse by the fact that most of us have our phones secured only by a four or six digit passcode. Even if you are using face id on your iPhone, it will still fall back to your passcode if it does not recognize you - which means all a criminal needs to gain access to almost everything in your digital life is your phone and passcode (see recent Wall Street Journal story on this topic).
I made too many changes here to detail them all, but a few worth noting include: using local encrypted backups instead of the cloud, turning on the iPhone stolen device protection, removing secure information from my photos (e.g. pictures of documents), increasing the complexity of my passcode, and always using face id instead of passcode in public.
Conclusions
I know it can be overwhelming to evaluate the myriad of options to secure your online accounts. I will confess that the scope of my project was made more complex by the fact I have been online for a long time (my Amazon account is celebrating its 27th birthday this year). But by following these 5 simple steps, anyone - no, really anyone - can quickly improve their online security and minimize the chance they end up a victim of one of the many attacks / scams happening today.